2. Basic knowledge of Javascript.
3. Basic knowledge of servers that how servers work.
4. And most important expertise in removing traces otherwise u have to suffer consequences.
Now First two things you can learn from a very famous website for basics of Website design with basics of HTML,SQL,PHP and javascript.
And for the fourth point that you should be expert in removing traces. I will explain this in my future tutorials. As we know traces are very important. Please don't ignore them otherwise you can be in big trouble for simply doing nothing. so please take care of this step.
2. CROSS SITE SCRIPTING
3. REMOTE FILE INCLUSION
4. LOCAL FILE INCLUSION
5. DDOS ATTACK
6. EXPLOITING VULNERABILITY
Cross site scripting (XSS) occurs when a user inputs malicious data into a website, which causes the application to do something it wasn’t intended to do. XSS attacks are very popular and some of the biggest websites have been affected by them including the FBI, CNN, Ebay, Apple, Microsoft, and AOL.
• Search Engines
• Login Forms
• Comment Fields
Remote file inclusion is the most often found vulnerability on the website.
Remote File Inclusion (RFI) occurs when a remote file, usually a shell (a graphical interface for browsing remote files and running your own code on a server), is included into a website which allows the hacker to execute server side commands as the current logged on user, and have access to files on the server. With this power the hacker can continue on to use local
exploits to escalate his privileges and take over the whole system.
RFI can lead to following serious things on website :
• Code execution on the web server
• Code execution on the client-side such as Javascript which can lead to other attacks such as cross site scripting (XSS).
• Denial of Service (DoS)
• Data Theft/Manipulation
4. LOCAL FILE INCLUSION
Let’s say a hacker found a vulnerable site, www.target-site.com/index.php?p=about, by means of directory transversal he would try to browse to the /etc/passwd file:
www.target-site.com/index.php?p= ../../../../../../../etc/password
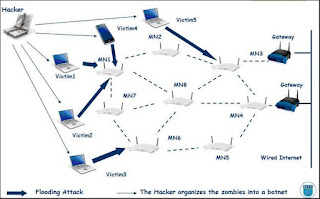
Simply called distributed denial of service attack. A denial-of-service attack (DoS attack) or distributed denial-of-service attack (DDoS attack) is an attempt to make a computer resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary,
it generally consists of the concerted efforts of a person or people to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely. In DDOS attack we consumes the bandwidth and resources of any website and make it unavailable to its legitimate users.









![Facebook redirect url trick injection vulnerability[TUT]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjLfczNRQSoZ3iLhcSNqKDKfPJ0zuIaUc9e8c_NxZEQVDjFYqvTqiTLgiabB7c5kTyPXDomxyeXhxGzYSk4dv09aImOjVEi2kfZBr3AOW_5Ym6hfQ8KaXaFoBQ2qie0jIvY-hEaAFIn77Sx/s200-c/Screenshot+%25284%2529.png)
